Bitcoin Hashing Visualization: Step by Step
Cryptographic and Computer Science World is full of complex concepts, but one theme is distinguished by its simplicity: hashing algorithms. Specifically
Basic
Hashing is a mathematical feature that takes input data (called “message”) and creates a fixed size output known as “hash”. In the case of SHA-256, which denotes a secure hash algorithm 256, this hash is usually 256 bit long. The purpose of the Mixing is to ensure the integrity and authenticity of the data, making it an essential component in digital transactions.
How Bitcoin Uses Hashing
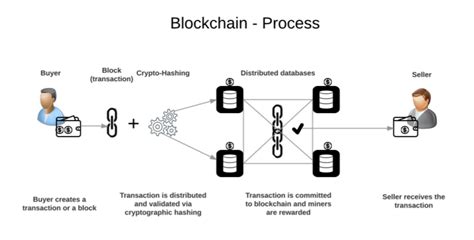
According to the official bitcoin wiki, Bitcoin uses the sha-256 algorithm to generate clearly random numbers in a way that requires a predictable amount of CPU efforts. This means that you are not needed for bitcoin transactions.
Step:
1
Message : the user creates a message that can be any piece of data such as transaction or information.
- This process involves several items using the hash algorithm rules and calculations.
.
Why Sha-256?
SHA-256 MP A Bitcoin Hashing Algorithm Choice Was Most Likely to Be Done:
1
Cryptographic strength : sha-256 is considered a safe and widely accepted cryptographic standard.
- Collision Resistance :
3
Pre -processing Resistance : The attacker is virtually impossible to find a certain entry entry that creates a certain output hash.
SHA-256 Visualization
To help illustrate how the sha-256 works, let’s create a simple example:
Imagine you have two fragments of information: “Hello, the world!” and hexadecimal code “1234567890abcdef”. To Generate Sha-256 hash for each information, you follow these steps:
1
Input : Turn both strings in hexadecimal format (eg 48656c6f20576f726c6421 for “hello, world!” And “and” 1234567890abcdef “in hexadekimal).
2.
.
Conclusion
The Sha-256 hashing algorithm used in Bitcoin is an essential component to ensure the integrity and authenticity of digital transactions. Cryptography.
Regardless of whether you are experienced cryptographer or just curious about cryptocurrency internal action, such as SHA-256 hashing algorithms world research can be both exciting and enlightened.